Port forwarding can be useful to ensure proper functioning and security of your web server/instances on cloud.
There are different types of port forwarding one can do :
- IPtables based port forwarding
- Web server based/proxy port forwarding.
All the above-mentioned solution serve the same purpose but choosing the right solution is important.
Let take a scenario to understand this better
Scenario 1: Port forwarding on localhost
Port forwarding traffic from port 80 to 443 port on the same instance
This is the most common scenario where your requirement to forward all the traffic from one port to another in the same instance for eg: port 80 to 443. It can be the case where you’re hosting an https website on an instance which listens on port 443 by default but would want to associate a domain name to instances’ IP. The fact that all the domain names refer to port 80 which in this scenario is not the case, instead everything is running on port 443.

To solve this you will need resolve domain name properly with https traffic which can be done by setting up port forwarding from 80 to 443.
The best way to do port forwarding will be to set up a web server proxy.
Steps to setup up port forwarding on web server :
In Apache, you can this using by modifying httpd.conf file.
Add following code at the end and restart Apache web server :
<VirtualHost *:80> ServerName www.bhargavamin.com Redirect / https://bhargavamin.com/ </VirtualHost>
In Nginx, you can do the same by modifying nginx.conf file.
server { listen [::]:80; return 301 https://$host$request_uri; }
This way you can route traffic internally on another port.
Note: A restart of the web server is a must after this changes.
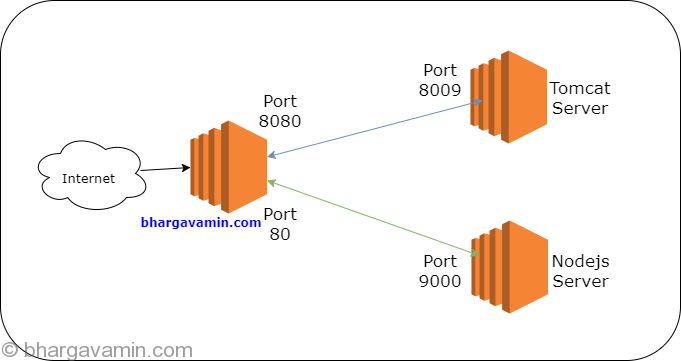
Scenario 2: Forward traffic to a remote host
Port forwarding traffic from port 80 to 3000 port of a remote host.
In this scenario, there will be a public facing host which will listen on port 80 and will internally forward all the traffic to private host (sitting in private subnet). This way you don’t expose your web server to the public and is considered to be more secure.

This type of port forwarding can be done in two ways:
- Via web server
- Via iptables
Via web server :
In Apache, you can forward all the traffic to different instance private ip by following below steps.
Go to httpd.conf file and copy paste below-mentioned code :
<VirtualHost *:80> ProxyPreserveHost On ProxyRequests Off ServerName www.bhargavamin.com ServerAlias bhargavamin.com ProxyPass / https://bhargavamin.com:80 ProxyPassReverse / http://172.31.16.101:3000 </VirtualHost>
This way Apache web server will forward all the traffic from port 80 to 3000 port of a remote instance.
In Nginx, you can do the same by copy-pasting following code in nginx.conf file :
server {
listen 80;
Server_name bhargavamin.com;
location / {
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header Host $http_host;
proxy_pass http://172.31.16.101:3000; }
}
Via IPtables:
You can also choose iptables to forward traffic to a remote host.
The difference between web server based port forwarding and iptables based port forwarding is that:
- Iptables forward all the packets bluntly without checking its headers in detail. You send any kind of traffic on a port, iptables rule will do its job and forwarding everything.
- Inward and outward traffic mapping: In iptables, you have to explicitly mention what and how an incoming or outgoing traffic routing is to be done. In other words determine rules for Pre-routing and Forwarding.
You can do iptables port forwarding by adding following rules in iptables:
# iptables -A PREROUTING -t nat -i eth0 -p tcp --dport 80 -j DNAT --to 172.31.16.101:3000 # iptables -A FORWARD -p tcp -d 172.31.16.101 --dport 3000 -j ACCEPT
The first rules will act as NAT that means it will send and receive traffic from 80 to remote host and the second rule will allow/accept traffic to be forwarded to remote host.
Note: For this rules to take effect you will need to save iptables rules by command sudo iptables save
You can also use iptables to forward SSH or RDP connection by making minor changes in above rules:
# iptables -t nat -A PREROUTING -p tcp --dport 3389 -j DNAT --to-destination 172.31.16.101:3389 # iptables -A FORWARD -p tcp --dport 3389 -j ACCEPT
Other AWS cloud based port forwarding solutions :
AWS provides managed services which takes care of all the tasks related to hosting an application to enabling port forwarding. AWS Elastic Load balancer(ELB) and Elastic Beanstalk are services which have port forwarding capability.
In ELB, you can create listeners which will do the traffic mapping for you. All you need is to add a listener rule in ELB. Find more about How to configure ELB listeners.
Elastic beanstalk provides a managed hosting platform which means when you deploy an application it automatically installs a web server, set preferred configs, create traffic forwarding and dns mapping by itself. Refer following documentation on how to create a Elastic beanstalk app.
At the end, one has to decide which type of port forwarding solution will helpful after looking at requirements.
Hope this helped!
Thanks for reading.











Social Profiles